This post is about the setup of a pfSense 2.0 firewall in transparent mode to connect and protect virtual machines hosted by OVH to the internet.
OVH provides failover IPs (fr) and RIPE IP Failover block (fr). These IPs and blocks can be re-routed between servers you are renting inside an OVH datacenter in 1min.
This make migration, failover and HA easy and at a low cost, no need to change something in the DNS or in the VM setup.
The setup and the use of these IPs is not easy. Adding a firewall in between don't help.To not increase the complexity of this post, the firewall is configured in transparent mode. This means that interfaces of the firewall are bridged.
What is a bridge ?
A network bridge fits between two networks and repeats Ethernet frames on one side to the other side and vice versa. A bridge works at layer 2 (Ethernet) of the OSI model (IP is layer 3) and ignores the IP settings. All type of Ethernet frames are forwarded by the bridge, even theses that encapsulate packets that are not related to the IP protocol. Bridges are smart and learn MAC addresses on both side to avoid to repeat frames that don't need to cross from one network to the other.Promiscuous mode
If you are using an hypervisor like VMware ESXi or Xen, you have to enable the promiscuous mode on each interfaces of the bridge to allow it to see all Ethernet frames and guess host on each side.Here is the procedure for VMware, ask Google if you use another hypervisor.
pfSense and bridging
The bridge connects multiple interfaces. Each of these interfaces can have an IP address, but this is not required. The Bridge itself can be attached to a network interface and have an IP address, but this is not required either. Here the goal is not to combine two networks in one but just to connect them without wasting any IP addresses or increasing complexity. Frames that contains IP packets can be filtered by the firewall rules. Here I'll bridge the WAN and the OPT1 (DMZ) interface. The LAN will be kept out of the bridge.pfSence can filter at the bridge level, but we want to filter at the member level. Check in the advanced settings of your FW that your setup match this one:

When do you need to allocate an OVH virtual MAC for your VM
I think the main purpose of the virtual MAC at OVH is to avoid MAC address conflict. This could be very annoying if your production server would stop working because someone is installing a new VM using a random MAC address that match your ! In the mean time they can use this to reinforce the security of their network.
Most of the time when you attache a failover IP to a virtual machine then you need to allocate a virtual MAC for this VM. But his is not always true. For example if you are attaching a second IP to an existing VM using the IP Alias approach, you don't need one because this second IP will use the MAC address of the primary address. Also If your VM is behind a router doing some Proxy ARP, the router use its own MAC address to masquerade your IP and the other side of the router it will be happy with any MAC address used by your VM.
This could be counter productive to allocate a MAC address when not needed, the OVH infrastructure could block the traffic when the MAC don't match the IP address. And if their are not doing that today they could do it later.
In the configuration bellow, you need to allocate a virtual MAC address for VMs going in the DMZ and for the firewall itself if you give it an IP address. No need of virtual MAC for VMs going in the LAN.
Giving a routable IP address to the firewall or not ?
Even if the bridge mode allows the firewall to do its job without giving it any IP address, the firewall need one to be managed using a web browser.For the early setup and for emergency access, I have the use to create a VM using a XUbuntu LiveCD distibution on the LAN side and use the VMware console to manage the firewall. The Firewall LAN side is configured with default address 192.168.1.1 and a working DHCP server, this make the network setup of the VM very easy. Just connect your browser to http://192.168.1.1, use admin / pfsense for login / password and you are in.
Giving a routable IP to the WAN side of your firewall would allow you to remotely manage your firewall and do hide NAT (masquerading) for the VMs connected to the LAN side (if any). This also allows you to upgrade and install new packages.
The challenge
Here is the "virtual" challenge I'll try to solve in this post. I'm using addresses from the private ranges to make my live easier for the demo but address in 10.x.x.x and 172.x.x.x must be viewed as routable address. 192.168.x.x are used for private network, like the LAN.
I have an OVH dedicated server with address 10.99.99.99/254 and its gateway at 10.99.99.254. OVH gives me a RIPE block of 8 addresses: 10.10.10.8/29 with the gateway at 10.10.10.14. I also have 2 single failover IPs 172.16.16.16/32 and 172.17.17.17/32.
I have an OVH dedicated server with address 10.99.99.99/254 and its gateway at 10.99.99.254. OVH gives me a RIPE block of 8 addresses: 10.10.10.8/29 with the gateway at 10.10.10.14. I also have 2 single failover IPs 172.16.16.16/32 and 172.17.17.17/32.
The RIPE block can be used in 2 different ways.
- The normal way is to use it as a subnet, with first address of the block reserved for the network and the last one for the broadcast address. Including the gateway address that is already allocated to an OVH router, this make 3 addresses unusable. If you have a /30 block (4 addresses) this make only one usable address for your host(s). The advantage of this setup is the simplicity of the network configuration of the hosts themselves.
- The other possibility is to use each address individually with a netmask of /32. You don't need to split your RIPE block in the OVH manager to works that way (this is what OVH say), just use each address like a single failover IP. When doing this, even if VMs are on the same switch, they are not on the same subnet anymore and traffic between them has to travel up to the default gateway and back. If you want a more direct path, you have to create a route between your VMs (see below). Also I thing this is better to use the RIPE gateway 10.10.10.10.14 than using the gateway of the physical host (10.99.99.254) because when moving the VMs and the RIPE block to another host, you don't need to change the VMs gateway. The inconvenient of this choice is that you have to configure your host network using the OVH guide (french).
Simple solution for the RIPE block
In this simple setup, I don't give any routable address to the firewall. The early setup must be done with the help of a VM installed on the LAN side.
First we need to enable and setup the WAN and DMZ (OPT1) interfaces to none. We will not attach any IP addresses to these interfaces (this time). We will bridge them. Bridge works one level below the Internet protocol and don't need any IP settings.
Then we are creating the bridge :
And setup the two members of the bridge using ctrl-click. This is the most difficult part :-)
The setup is done. Yes don't be afraid this is enough. Now we have to setup the filter rules. I give you some sample rules, but use your owns.
First I like to be able to ping in any direction, at least for the setup and troubleshooting.
I want to give unrestricted internet access to VMs in the DMZ. Anyway I'm adding a restriction for the LAN. The DMZ can be accessed by the internet (demilitarized zone) and can be compromised. This is why the DMZ cannot have more access rights to access the LAN than the Internet.
Here are all the details :
Now I suppose I want to host a mail server on 10.10.10.9 and need to let SMTP packets go in..
Here are the details of the SMTP setup.
Now the most important part is the network setup of 10.10.10.9. Nothing difficult anyway :
IP_ADDR=10.10.10.9Network setup for other hosts of the RIPE block are similar.
NETMASK=255.255.255.248 (/29)
GATEWAY=10.10.10.14
Add a single failover IP to the DMZ
Now I want to add a host with a single failover IP 172.16.16.16/32 to the DMZ. I just need to setup the filter rules like the SMTP rule above for this new host. Nothing more is required because we are working in bridge mode.On the other hand, the setup of the host itself is more tricky, not because of the firewall, but because of how failover IP works. Follow the OVH guide (french) to setup your new host using 172.16.16.16 as the failover IP and 10.99.99.254 for the gateway (the one ending in .254).
In this configuration, traffics between 10.10.10.9 and 172.16.16.16 has to go up to the OVH router and then back to the destination. In both case the traffic has to pass through the firewall that must have a rules to let the traffic goes out and in. This is because hosts ignore they are side by side. If you expect to have a lot of traffics and want to speed it up, you have to add routes between the hosts themselves. Don't think that the fact that your traffics between host inside the DMZ goes trough the firewall increase the security. If a pirate is able to hack one of your VM inside the DMZ, he is able to bypass the firewall to attack your other hosts too.
Here are sample command lines for linux and windows. You have to hard-code these routes in the hosts configurations.
On 172.16.16.16, add a route to network 10.10.10.8/29
linux: route add -net 10.10.10.8 netmask 255.255.255.248 dev eth0
windows: route -p ADD 10.10.10.8 MASK 255.255.255.248 172.16.16.16
On 10.10.10.9 add a route to host 172.16.16.16/32
linux: route add -host 172.16.16.16 netmask 255.255.255.255 dev eth0
windows: route -p ADD 172.16.16.16 MASK 255.255.255.255 10.10.10.9
Attach an IP to the WAN side
This makes the firewall remotely manageable and allows to give an internet access to the LAN side.I choose 10.10.10.13/29 from the RIPE block, in the next section I explain how to use a single failover IP instead.
I go to the WAN interface configuration to setup the IP and its gateway at once.
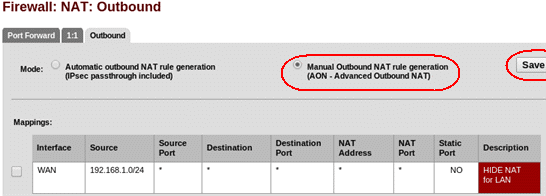
Now I masquerade the LAN addresses using hide NAT to give Internet access to the LAN side. Don't forget to switch to manual, I don't want to NAT hosts in the DMZ.
The details:
I also need to check that the LAN has a rule that give access to the internet :
Done !
If you want, you can forward some ports to hosts inside the LAN.
You can reach host in the DMZ from LAN.
Attach a single failover IP to the WAN side
If you don't have a RIPE block or prefer to use a single failover IP instead, then read this section.This setup cannot be configured easily using the pfSense GUI interface, some tricks are required.
Here is the plan, first get an Internet access using some hand written command lines. Then download and install the Shellcmd package. Finally hard code the command line to make the setup persistent.
First setup the WAN IP without any gateway :
Then setup the default gateway manually. I choose to use the Command Prompt interface of the GUI. Use the two commands :
route add -net 10.99.99.254/32 -iface em0
route add default 10.99.99.254
If you don't know where 10.99.99.254 is coming from, re-read the beginning of this article.
Don't forget to setup a working DNS to have a fully working internet connection. I choose the Google public DNS.
Now the firewall should have internet access and we can install package Shellcmd.
Then hard code the two commands above inside Shellcmd to get the make config persistent.
You can try to reboot, just to see if the config works and setup hide NAT for the LAN side as explained above.
Funny things
It looks like the OVH gateway works like an universal ARP proxy or Captive portal. I means my OVH gateway replies to any ARP request. This means that for any given a.b.c.d/32 failover IP, I can setup a host or virtual host using a mask /24 (instead of /32) and a.b.c.X where X can be anything not in ( 0, 255 or d ) for my gateway.And it works on my Kimsufi server.
I think this is how OVH setup some (maybe all) of their routers to be able to support migration of failover IP or block without too much headache.
What is fun is to traceroute some IPs in a.b.c.* and see that they are not directly attached to the WAN but are behind some routers.
OVH don't say anything about this setup and then this feature is funny but cannot be used on a production server.
Be careful if you use a wrong setup and generate a lot of unexpected ARP requests, OVH monitor ARP request and can warn you to quickly fix the problem or even disable your network link.





















No matter what I try I can not get a client (virtualized WinXP as a test) to access the internet using "Attach a single failover IP to the WAN side" method.
ReplyDeleteMy client (on 192.168.1.0/24 LAN) can ping the LAN interface and the WAN interface, and can even resolve FQDN (DNS is pointed at pFsense) but can not make any connections.
A tracert fails after the first hop (192.168.1.1 LAN interface on pFsense)
From pfSense itself I'm able to ping and access the internet without issue. I have shellcmd installed, and the rules seemingly hold after a reboot. I'm not sure if it's my NAT rules...
Firewall LAN rule is enabled.
This is probably a NAT problem. You must have the same NAT setup and filter rules as in "Attach an IP to the WAN side".
ReplyDeleteI tried that originally (or so I thought?). I went back and re-applied the NAT settings, w/o a configuration change and it worked! Perhaps it wasn't saving/applying, or more likely... user error.
DeleteThanks for this write-up!
Hello,
ReplyDeleteI have configured my infrastructure like your How-To, everything is fine but i've a little problem : When I'm Connected from VPN (or LAN), I can't ping or access to a VM in DMZ (with a FailOver IP).
Note : Is Ok From WAN Adress, this problem occured only with LAN or VPN.
The traceroute (from VPN 172.16 Subnet):
1 26 ms 26 ms 28 ms 172.16.0.1
2 27 ms * * vss-1b-6k.fr.eu [94.23.38.252]
3 * * * Délai d'attente de la demande dépassé.
4 * * * Délai d'attente de la demande dépassé.
The connexion stop at vss-1b-6k.fr.eu (or maybe at the pfsense firewall ??)
Can you Help ?
Thanks
Which VPN are you using ?
ReplyDeleteWhat do you mean by "this problem occurred only with LAN " which LAN ? The LAN side of your FW or LAN at home or the office ? What is not working ?
Hello, Thanks for the reply.
DeleteI Use OpenVPN.
I've 4 network :
WAN : with my Public FailOver IP
LAN : 10.0.0.0/16 for VMs with NAT (No FailOver on It)
DMZ : Only for VM With IP FailOver, bridged on WAN
OpenVPN : 172.16.0.0/24 for my VPN clients.
From the a VM on the LAN (10.0.0.0) or from VPN Client (172.16.0.0), I can Ping and access what I want in Internet but When I want ping or access an IP in the DMZ, this error occured. (with the traceroute of my previous message).
Sorry for the english, I'm French :)
Thanks for your support.
Did you find a solution for this?
DeleteI'm having the same problem: traffic from LAN is succesfullt NATted and external websites are accessible. Traffic from LAN to DMZ/OPT is not forwarded somehow. The firewall shows no info whatsoever. Mindboggling!
The LAN should have access to the DMZ.
ReplyDeleteYou should first fix this problem before to think about the VPN.
Did'you setup the "ping in any direction" rule ? Do you have restrictions on the LAN side? To the internet or the DMZ ?
From the VPN, do you have access to the VMs in the LAN ?
Hi Alain,
DeleteI'm faced the same problem as
"Mathieu GILLOOTS" and "luca scarano30"
can't reach dmz from my lan network.
folowed exactly by your instructions
could you advice anything please ?
thank you
Yes I have the "ping in any direction"
ReplyDeleteI does'nt have any restriction, just a fresh config like your HowTo. (+ My rules for HTTP, SMTP, ... servers).
Lan to Internet : OK
Lan <=> VPN : OK
VPN to internet : OK
DMZ <=> Internet : OK
VPN or LAN <=> DMZ : No OK
Like I see in the traceroute, the packets out to the OVH Router then they could'nt IN my pfsense.
I'm planning to implement your solution at Online (Dedibox) with IP Failover.
ReplyDeleteBut in the Online docs, they wrote :
"Important : Ne jamais faire de bridge sur votre carte réseau Dedibox. Vous risqueriez de diffuser sur le réseau une adresse MAC virtuelle, ce qui provoquerait la mise en sécurité de votre port réseau et la suspension de votre serveur. Faites uniquement du NAT ou du mode routé !"
What do you think about it ?
If dedibox don't give you any virtual MAC address that they will not "blacklist" you cannot run a virtual firewall in bridge mode.
DeleteOK. I generated virtual mac addresses for all my failover ips in the dedibox console. So i have to associate each one to the corresponding virtual interface ?
DeleteIf dedibox provides virtual MAC addresses, then give them a try.
ReplyDeleteBe carefull, if you chnage the mac address of already installed VMs , the OS will recognize the Network adapter as a new one and will probably not reuse the configured of the "old" one.
All right. I will try this. In the worse case my new servers will be blocked for a while but my old one will do the job.
DeleteI will give you some feed back.
Thank you for this post. I deployed my new server with pfSense and one VM in the DMZ.
DeleteAs Dedibox provides virtual MAC adresse for my VM, all work well !
Wow, after spending half the night on it I managed to install an OVH server with Esxi, a vm inside with pfsense using a failover IP, and an other vm behind (web server) -this one now can see the internet at last.
ReplyDeleteNow I'll install Pound on pfsense to use it as a proxy to reach the web server, but I feel it's correctly protected - being hidden from the Net.
I just used one trick you don't use - it avoids installing a PC with a browser on the LAN leg to manage pfsense: at beginning,
- start the pfsense vm
- connect using the console from vsphere client
- install the 2 routes - adding the MAC address:
route add -net 10.99.99.254/32 -iface em0:abceef0102 (remove dots)
route add default 10.99.99.254
- then setup a rule to access Webconfigurator from my home/admin PC:
easyrule pass wan tcp my.hom.e.ip fai.lov.er.ip 443
So I can connect and go on with the install
I forgot the most important part : MERCI !
ReplyDeleteMy scenario is similar:
ReplyDeleterouter nat to external esxi
v
v
external linux eth with iptables (virtual machine)
this is connected to a vshpere switch
v
v
internal linux eth connected to a second vshpere switch vlan 100
promiscuous mode as you mentioned in the tutorial
v
v
in the same switch connected WAN pfsense vlan 100 promiscuos mode
v
v
in another vshpere switch connected LAN pfsense
v
v
in this last switch connected all the DMZ
Not working :-(
Thanks so much.
ReplyDeleteWorked brilliantly.
Hello,
ReplyDeletei've the same problem of Mathieu GILLOOTS.
My configuration is:
- DMZ host with failover ip and mac set from ovh, connected to dmz switch
- DMZ interface of the firewall without ip, bridged with external eth
- external eth without ip and connected to the public switch
- LAN and VPN with private ip
- WAN dedicated interface for the firewall (also gateway for the lan)
LAN/VPN --> internet = ok
WAN --> internet = ok
DMZ host --> internet = ok
WAN --> DMZ host = ok
internet --> WAN = ok
internet --> DMZ = ok
LAN --> DMZ = NOT WORK
So, all work but no the lan to dmz host connection.
The rules are set permissive from lan but i don't see any packet filtered in dmz host's interface.
Thank you
Hi,
ReplyDeleteGreat tutorial. The theory is usefull and working.
But besides that PfSense is not doing the job for me.
When everything is configured PfSense (both i386 andamd64) will become unavailable after some time. It sucks up all available CPU on my vSphere host.
If I don't limit it, it will affect other VM's.
When I check further... I see 100% CPU usage used by interface's taskq process according to the system activity monitor in the webinterface.
PfSense will become unavailable.
I have not configured any heavy traffic-using VM's on the DMZ nor LAN so I do not know what is causing this problem.
Other problem was OVH flooding me about arp who-has scans when using the gateway of the ripe-block.
Fixed this with ifconfig em0 staticarp
If anyone has a solution or (better) alternative (appliance) for me, please let me know.
Thanks in advance,
Jesper
Forgot I was using vSphere 5.1 and seperated all interfaces onto different Virtual Networks on the available vmnic.
DeleteUsed PfSense 2.1 Full Install from LiveCD.
I now use vyatta, a iOS like software for my routers
ReplyDeleteHi Mathieu,
DeletevYatta is great but they removed web-based support from the open source appliance unfortunately.
Users with less knowledge need to be able to use it also; thus a webinterface is a requirement.
Thanks,
Jesper
Hi. I am an old folk of m0n0wall and PFSense since firts versions. I used your guide for getting the idea and then made my own deployment. Not very different, just a couple of changes. But OVH thought it was a bad move, so they blocked my machine. Just take care. Seems that new datacenter in Gravelines has some other routing system.
ReplyDeleteTask Type
Incident
Category
the whole network
Status
CLOSED
Percent Complete
100%
Details
We have an incident on the dedicated routing in Gravelines.
Date: Monday, 16 December 2013, 19:08PM
Reason for closing: Done
Additional comments about closing: The traffic towards some dedicated server networks was affected by some abnormal traffic on one of the VLAN clients. The machine concerned has been isolated from the network.
Hi!
ReplyDeleteJust wanna say thanks, I've been mandated to give SyS hosted solutions (a sub of OVH) a try and come up with a working setup! Following this post - which is thoroughly well done btw! - and you helped me a lot making it work!
Cheers!
Hi!
ReplyDeleteJust wanna say thanks, I've been mandated to give SyS hosted solutions (a sub of OVH) a try and come up with a working setup! Following this post - which is thoroughly well done btw! - and you helped me a lot making it work!
Cheers!
I feel so much smarter now. I like the trend that content is becoming more and more important.I like the trend that content is becoming more and more important.
ReplyDeleteVMware Training in Chennai
Gateway Firewall solutions Hyderabad, India | Cloudace
ReplyDeleteCloud Ace Technologies is offering Implementation Services on Cloud Computing, Cloud Services, IT Security, Storage solutionsGateway Firewall solutions Hyderabad,
I read that Post and got it fine and informative.
ReplyDeletevmware courses london
Nice post! This is a very nice that I will definitively come back to more times this year! Thanks for informative post. VPS Hosting
ReplyDeleteNice post! This is a very nice that I will definitively come back to more times this year! Thanks for informative post. Managed IT Services
ReplyDeletethank you for sharing amazing post.yahoo com mail nice post
ReplyDeleteYour very own commitment to getting the message throughout came to be rather powerful and have consistently enabled employees just like me to arrive at their desired goals.
ReplyDeletepython training Course in chennai
python training in Bangalore
Python training institute in bangalore
Really excellent blog...
ReplyDeleteaws training in bangalore
Really excellent blog...
ReplyDeleteaws training in bangalore
artificial intelligence training in bangalore
machine learning training in bangalore
blockchain training in bangalore
iot training in bangalore
artificial intelligence certification
artificial intelligence certification
Hi, Great.. Tutorial is just awesome..It is really helpful for a newbie like me.. I am a regular follower of your blog. Really very informative post you shared here. Kindly keep blogging.
ReplyDeleteAWS training in chennai
AWS Training in Bangalore
Wow !! Really a nice Article. Thank you so much for your efforts. Definitely, it will be helpful for others. I would like to follow your blog. Share more like this. Thanks Again
ReplyDeletehonor mobile service center
honor mobile service centre in Chennai
honor service center near me
honor service
honor service centres in chennai
honor service center velachery
honor service center in vadapalani
I think this is the best article today. Thanks for taking your own time to discuss this topic, I feel happy about that curiosity has increased to learn more about this topic. Keep sharing your information regularly for my future .
ReplyDeleteredmi service center in t nagar
This information is impressive; I am inspired with your post writing style & how continuously you describe this topic. After reading your post, thanks for taking the time to discuss this, I feel happy about it and I love learning more about this topic.
ReplyDeletecoolpad service center chennai
This is the exact information I am been searching for, Thanks for sharing the required infos with the clear update and required points.
ReplyDeleteapple service center in chennai
Hi! Thank you for the share this information. This is very useful information for online blog review readers. Keep it up such a nice posting like this.
ReplyDeletemotorola service center in velachery
Alot of blogs I see these days don't really provide anything that I'm interested in, but I'm most definitely interested in this one. Just thought that I would post and let you know. Nice! thank you so much! Thank you for sharing.
ReplyDeletemi service center in chennai
This comment has been removed by the author.
ReplyDeleteWonderfull blog!!! Thanks for sharing with us...
ReplyDeletePython Training in Bangalore
Best Python Training in Bangalore
Python Training in Coimbatore
Python Training Institute in Coimbatore
Python Course in Coimbatore
Software Testing Course in Coimbatore
Spoken English Class in Coimbatore
Web Designing Course in Coimbatore
Tally Course in Coimbatore
Truly good job!!! The admin was providing the useful post and I like to you additional info from your blog. Thank you...
ReplyDeleteTableau Training in Chennai
Tableau Certification in Chennai
Pega Training in Chennai
Primavera Training in Chennai
Unix Training in Chennai
Power BI Training in Chennai
Job Openings in Chennai
Excel Training in Chennai
Tableau Training in Vadapalani
Tableau Training in Thiruvanmiyur
I have read your excellent post. Thanks for sharing
ReplyDeleteaws training in chennai
big data training in chennai
iot training in chennai
data science training in chennai
blockchain training in chennai
rpa training in chennai
security testing training in chennai
I am really enjoying reading your well-written articles. It looks like you spend a lot of effort and time on your blog. I have bookmarked it and I am looking forward to reading new articles. Keep up the good work.
ReplyDeletePHP Training in Coimbatore
PHP Training Institute in Coimbatore
best selenium training in coimbatore
Python Classes in Coimbatore
android app development course in coimbatore
embedded systems course in coimbatore
German Language course in Coimbatore
Selenium course in coimbatore
Java Training in Bangalore
Nice post... Thank you for sharing..
ReplyDeleteBest Python Training in Chennai/Python Training Institutes in Chennai/Python/Python Certification in Chennai/Best IT Courses in Chennai/python course duration and fee/python classroom training/python training in chennai chennai, tamil nadu/python training institute in chennai chennai, India/
thanks for sharing this information
ReplyDeleteandroid training institutes in coimbatore
ios training in coimbatore
amazon web services training in coimbatore
aws training in coimbatore
big data training in coimbatore
hadoop training in coimbatore
nice blog
ReplyDeleteget best placement at VSIPL
digital marketing services
Web development Services
seo network point
Excellent information with unique content and it is very useful to know about the AWS.aws training in bangalore
ReplyDeleteThis post is really nice and informative. The explanation given is really comprehensive and informative . Thanks for sharing such a great information..Its really nice and informative . Hope more artcles from you. I want to share about the best best java tutorial videos with free bundle videos providedand java training .
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteWe as a team of real-time industrial experience with a lot of knowledge in developing applications in python programming (7+ years) will ensure that we will deliver our best in python training in vijayawada. , and we believe that no one matches us in this context.
ReplyDeleteGreat efforts put to publish these kinds of articles that are very useful to know. I’m thoroughly enjoying your blog. And Good comments create great relations. You’re doing an excellent job. Keep it up.
ReplyDeleteMagento Development Training Course in Chennai Zuan Education
Selenium Training Course in Chennai Zuan Education
Nice post. Thanks for sharing...
ReplyDeleteAWS Training in Bangalore
ReplyDeleteWhatever we gathered information from the blogs, we should implement that in practically then only we can understand that exact thing clearly, but it’s no need to do it, because you have explained the concepts very well. It was crystal clear, keep sharing..
aws course in bangalore
amazon web services tutorial
Excellent web site you have got here.. It’s hard to find excellent writing like yours nowadays.lap I truly appreciate people like you! Take care!!
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteThanks for the informative article About Java.This is one of the best resources I have found in quite some time. Nicely written and great info. I really cannot thank you enough for sharing.
ReplyDeleteJava training in chennai | Java training in annanagar | Java training in omr | Java training in porur | Java training in tambaram | Java training in velachery
I blog frequently and I really appreciate your content. Your article has really peaked my interest. I am going to bookmark yourtechnology website and keep checking for new details about once per week. I subscribed to your RSS feed too.
ReplyDeleteBlogging is an art and you have become an eminent artist by writing this stupendous blog. I thank you for sharing this wonderful insight. Web Designing Course Training in Chennai | Web Designing Course Training in annanagar | Web Designing Course Training in omr | Web Designing Course Training in porur | Web Designing Course Training in tambaram | Web Designing Course Training in velachery
ReplyDeletepython training in bangalore | python online training
ReplyDeleteaws training in Bangalore | aws online training
artificial intelligence training in bangalore | artificial intelligence online training
machine learning training in bangalore | machine learning online training
data science training in bangalore | data science online training
The admin was providing the useful post and I like to you additional info from your blog. Thank you...AWS training in Chennai
ReplyDeleteAWS Online Training in Chennai
AWS training in Bangalore
AWS training in Hyderabad
AWS training in Coimbatore
AWS training
Hi, Great.. Tutorial is just awesome..It is really helpful for a newbie like me.. I am a regular follower of your blog. Really very informative post you shared here. Kindly keep blogging.
ReplyDeleteArtificial Intelligence Training in Chennai | Certification | ai training in chennai | Artificial Intelligence Course in Bangalore | Certification | ai training in bangalore | Artificial Intelligence Training in Hyderabad | Certification | ai training in hyderabad | Artificial Intelligence Online Training Course | Certification | ai Online Training | Blue Prism Training in Chennai | Certification | Blue Prism Online Training Course
I am feeling great to read this.you gave a nice info for us.
ReplyDeleteplease update more.
Web designing and development Training in Coimbatore | HTML Training in Coimbatore| React JS Training in coimbatore | Online React JS Training in coimbatore| Web Development Training in Coimbatore | Online Web Development Training in Coimbatore | Web Designing Course in Saravanampatti | Web Development Institute in Coimbatore | Web Designing Training in Saravanampatti | Online Web Designing Training in Saravanampatti
Good Post! , it was so good to read and useful to improve my knowledge as an updated one, keep blogging. After seeing your article I want to say that also a well-written article with some very good information which is very useful for the readers....thanks for sharing it and do share more posts like this. https://www.3ritechnologies.com/course/salesforce-training-in-pune/
ReplyDeletenice article....keep up
ReplyDeleteCreo centre in coimbatore | Creo course in coimbatore | Creo course fees in coimbatore | Creo course training in coimbatore | Best creo course in coimbatore | creo course training with placement in coimbatore | creo online training course in coimbatore | Creo online course in coimbatore | Creo fees structure in coimbatore | Creo jobs in coimbatore | Creo training in coimbatore | Cadd centre in coimbatore | Cadd courses in coimbatore | Cadd centre fees structure in coimbatore
thanks for give informative content...
ReplyDeleteBest Selenium training course in coimbatore | Best Selenium training in coimbatore | Selenium training with placement in coimbatore | Selenium online certification in coimbatore | Selenium online course in coimbatore | Selenium training fees in Qtree Technologies in coimbatore | Selenium training in coimbatore Quora | Selenium online class in coimbatore | Selenium course in coimbatore | Selenium training centre in coimbatore | Selenium training and placement in coimbatore
This comment has been removed by the author.
ReplyDeleteonline classrooms for teachers
ReplyDeletelms online school
best education platforms
lms higher education
virtual learning platforms
Best IT Training in Chennai
ReplyDeleteJava will help you design games and some fabulous games too
ReplyDeletejava full stack developer course,
java training in bangalore,
best java training institutes in bangalore
Software IT Coaching Center in Chennai
ReplyDeleteThe content on your blog was really helpful and informative. Thakyou. # BOOST Your GOOGLE RANKING.It’s Your Time To Be On #1st Page
ReplyDeleteOur Motive is not just to create links but to get them indexed as will
Increase Domain Authority (DA).We’re on a mission to increase DA PA of your domain
High Quality Backlink Building Service
1000 Backlink at cheapest
50 High Quality Backlinks for just 50 INR
2000 Backlink at cheapest
5000 Backlink at cheapest
Good Post! Thank you so much for sharing this pretty post, it was so good to read and useful to improve my knowledge as updated one, keep blogging. Primavera P6 Certification Training in Chennai | Primavera Training in India
ReplyDeleteWe are used to the fact that we know only religious and public holidays and celebrate only them.Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder Iamlinkfeeder
ReplyDeleteAnnabelle loves to write and has been doing so for many years.Backlink Indexer My GPL Store Teckum-All about Knowledge
ReplyDelete
ReplyDeleteBuy top quality handguns, rifles, shortguns and other firearms and have them shipped discreetly to your address.
We do same day shipment, and tracking information is
provided as soon as shipment is made.
All products come with manual and most of them are still in box but not all are brand new.
These are not stolen and there’s a
sales document issued for each.
We also ship to an FFL for those who prefer it that way.
Please feel free to visit our website https://www.legitarmsdealer.com/
smith-wesson-mp-shield
6-5-creedmoor-ammo
savage-10pt-sr-308-for-sale
https://www.buycounterfeitbills.com/
http://goldenretrievers.company.com https://parottdise.com
Hızlı takipçi almak için takipçi satın al
ReplyDeleteOrganik takipçi almak için takipçi satın al
Bilgisayardan takipçi almak için takipçi satın al
Mobil cihazdan takipçi almak için takipçi satın al
Gerçek ve orijinal takipçi almak için takipçi satın al
Yazarkasa ile takipçi almak için takipçi satın al
Bitcoin takipçi almak için takipçi satın al
Pos ile takipçi almak için takipçi satın al
EFT ile takipçi almak için takipçi satın al
Havale ile takipçi almak için takipçi satın al
Mobil ödeme ile takipçi almak için takipçi satın al
Tamamı orijinal takipçi almak için takipçi satın al
Organik ile takipçi almak için takipçi satın al
Türkiye takipçi almak için takipçi satın al
Global takipçi almak için takipçi satın al
En hızlı instagram takipçi satın al
En uygun instagram takipçi satın al
En telafili instagram takipçi satın al
En gerçek spotify takipçi satın al
En ucuz instagram takipçi satın al
En otomatik instagram takipçi satın al
En sistematik tiktok takipçi satın al
En otantik instagram takipçi satın al
En opsiyonel instagram takipçi satın al
En güçlü instagram takipçi satın al
En kuvvetli instagram takipçi satın al
En seri instagram takipçi satın al
En akıcı instagram takipçi satın al
En akıcı instagram takipçi satın al
En akıcı instagram takipçi satın al
En akıcı instagram takip etmeyenler
Liên hệ Aivivu, đặt vé máy bay tham khảo
ReplyDeletevé máy bay đi Mỹ
giá vé máy bay từ mỹ về việt nam tháng 12
thông tin chuyến bay từ canada về việt nam
vé máy bay từ nhật về việt nam bao nhiêu tiền
Chuyến bay từ Hàn Quốc về Việt Nam
Vé máy bay từ Đài Loan về VN
chuyen bay chuyen gia ve viet nam
Welcome to CapturedCurrentNews – Latest & Breaking India News 2021
ReplyDeleteHello Friends My Name Anthony Morris.latest and breaking news drupepower.com
Redmi is tipped to launch the Redmi K50 series in February 2022. Which means this phone launch next in starting in February .click here for this news Redmi K40 Gaming Gets Approved In China
ReplyDeleteFor All News Click Here Nindia24
The docs helped me a lot in enhancing my Knowledge..,Thank You.I want to share aboout Agro Fertilizer Company in India
ReplyDeleteHow To Get Free Data On Mobile Using Secret Trick
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteMmorpg oyunlar
ReplyDeleteinstagram takipçi satın al
TİKTOK JETON HİLESİ
tiktok jeton hilesi
Sac Ekim Antalya
Takipci
İnstagram Takipçi Satın Al
mt2 pvp
ınstagram takipci
smm panel
ReplyDeleteSmm Panel
Https://isilanlariblog.com
İnstagram Takipçi Satın Al
HİRDAVATCİBURADA.COM
BEYAZESYATEKNİKSERVİSİ.COM.TR
SERVİS
Tiktok hile
uc satın al
ReplyDeletenft nasıl alınır
en son çıkan perde modelleri
yurtdışı kargo
minecraft premium
en son çıkan perde modelleri
lisans satın al
özel ambulans
Realme 9i Receiving Realme UI A.11 OTA Update With Jio 5G Support
ReplyDelete